GCP – What’s new in Cloud Armor: Innovations to boost security posture, threat protection
In today’s complex threat landscape, effectively managing network security is crucial — especially across diverse environments. Organizations are looking to advanced capabilities to strengthen security, enhance threat protection, and simplify network security operations for hybrid and multicloud deployments.
We’re excited to announce new capabilities in Cloud Armor, featuring more comprehensive security policies and granular network configuration controls and improvements, so you can more easily manage network security operations across hybrid and multicloud environments.
Improving your security posture with hierarchical security policies and organization-scoped address groups
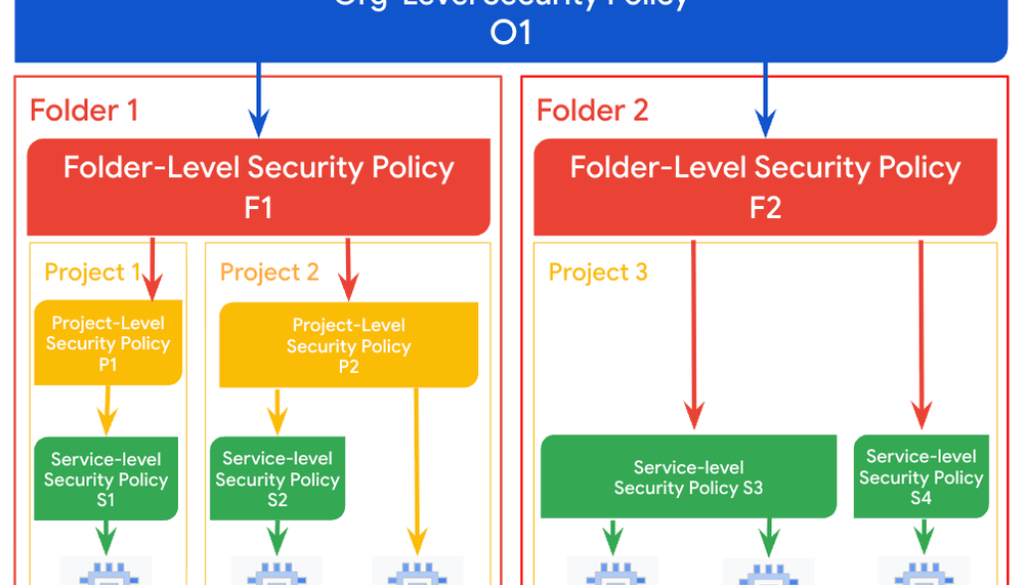
Hierarchical Security policies, now generally available, can extend Google Cloud Armor’s web application firewall (WAF) and DDoS protection by allowing security policies to be configured at the organization, folder, and project level. This update can help manage security policies across projects in large organizations with centralized control to support a consistent security posture and streamlined deployment of updates and mitigations.
Organization-scoped address groups, now generally available, can help manage IP range lists across multiple Cloud Armor security policies. Organization-scope address groups can enhance scalability and manageability by enabling the definition and reuse of IP range lists for both hierarchical and project-level configurations.
You can reduce the complexity of cloud networking security configurations by using organization-scoped address groups to eliminate duplicate rules and policies across multiple backends as well as share it across products such as Cloud Next Generation Firewall for a unified and consolidated security posture.
Security Policies overview.
Enhancing threat protection with granular network policy controls
Threat actors frequently conceal malicious content in larger request bodies to circumvent detection. Our enhanced WAF inspection capability, now in preview, incorporates the expansion of request body inspection from 8 KB to a robust 64 KB for all preconfigured WAF rules. This leap in inspection depth dramatically improves the capacity to detect and mitigate sophisticated malicious content.
JA4 network fingerprinting support, now generally available, elevates SSL/TLS client fingerprinting with more detailed and precise client identification and profiling, while building on the foundational principles of JA3.
JA4 incorporates additional fields and metadata, and can yield deeper insights into client behavior. This advanced telemetry can provide security analysts with richer contextual information, facilitating more sophisticated security analysis, more thorough threat hunting, and the ability to differentiate legitimate traffic from malicious actors.
Our Media CDN layer is essential for maintaining optimal performance and availability. To help protect it from malicious traffic, Cloud Armor now supports Network Threat Intelligence (NTI) and Autonomous System Number (ASN) for Media CDN, now generally available.
This new capability can strengthen security against known malicious IP addresses and traffic patterns by permitting and blocking traffic from specific ASNs directly at the network edge. Effectively, this can preempt the impact of known malicious entities on your services. It represents a potent instrument for safeguarding media assets and ensuring a secure user experience.
The global front end: Your unified defense strategy
Google Cloud’s global front end (GFE) provides comprehensive protection for your workloads no matter where they’ve been deployed — on Google Cloud, on other public cloud environments, in co-location facilities, or on-premises data centers. The GFE integrates Cloud Load Balancing, Cloud Armor, and Cloud CDN into a singular, end-to-end solution at the perimeter of the Google Cross-Cloud Network.
Our GFE offering can help ensure the secure, reliable, and high-performance delivery of defensive services to the internet. Functioning as the dedicated security component in the GFE, Cloud Armor is your primary line of defense, protecting applications and APIs from a broad spectrum of web and DDoS attacks. It also can manage your network security posture, safeguarding against the OWASP Top 10 vulnerabilities, and mitigating bot and fraud risks with reCAPTCHA Enterprise integration.
Google Cloud global front end.
Industry recognition and sustained customer confidence
Google Cloud Armor’s commitment to innovation and client success has garnered significant recognition. We are honored that Cloud Armor was acknowledged as a “Strong Performer” in The Forrester Wave™: Web Application Firewall Solutions, Q1 2025.
Forrester’s rigorous evaluation cited Google Cloud Armor’s vision and roadmap that emphasize protection and automation, with a strong focus on AI. The report also recognized Google’s streamlined operations facilitated by Gemini, and differentiated custom reporting.
The report cited Cloud Armor’s threat intelligence feeds and DevOps integrations, enabling robust security in your development pipelines. The report also noted Cloud Armor’s flexible pricing and the Cloud Armor Enterprise tier that includes threat intelligence and DDoS protection as a bundled solution.
The Forrester Wave™: Web Application Firewall Solutions, Q1 2025
Get started with Cloud Armor
With these advanced capabilities, Google Cloud Armor can empower organizations to significantly enhance their security posture and threat protection while embracing a proactive, intelligent, and unified approach to safeguarding their assets.
You can learn more about how Google Cloud Armor can transform your security posture here.
Forrester does not endorse any company, product, brand, or service included in its research publications and does not advise any person to select the products or services of any company or brand based on the ratings included in such publications. Information is based on the best available resources. Opinions reflect judgment at the time and are subject to change. For more information, read about Forrester’s objectivity here.
Read More for the details.