GCP – ViewState Deserialization Zero-Day Vulnerability in Sitecore Products (CVE-2025-53690)
Written by: Rommel Joven, Josh Fleischer, Joseph Sciuto, Andi Slok, Choon Kiat Ng
In a recent investigation, Mandiant Threat Defense discovered an active ViewState deserialization attack affecting Sitecore deployments leveraging sample machine keys that had been exposed in Sitecore deployment guides from 2017 and earlier. An attacker leveraged the exposed ASP.NET machine keys to perform remote code execution.
Mandiant worked directly with Sitecore to address this issue. Sitecore tracks this vulnerable configuration as CVE-2025-53690, which affects customers who deployed any version of multiple Sitecore products using sample keys exposed in publicly available deployment guides (specifically Sitecore XP 9.0 and Active Directory 1.4 and earlier versions). Sitecore has confirmed that its updated deployments automatically generate unique machine keys and that affected customers have been notified.
Refer to Sitecore’s advisory for more information on which products are potentially impacted.
Summary
Mandiant successfully disrupted the attack shortly after initiating rapid response, which ultimately prevented us from observing the full attack lifecycle. However, our investigation still provided insights into the adversary’s activity. The attacker’s deep understanding of the compromised product and the exploited vulnerability was evident in their progression from initial server compromise to privilege escalation. Key events in this attack chain included:
-
Initial compromise was achieved by exploiting the
ViewState DeserializationvulnerabilityCVE-2025-53690on the affected internet-facingSitecoreinstance, resulting in remote code execution. -
A decrypted ViewState payload contained WEEPSTEEL, a malware designed for internal reconnaissance.
-
Leveraging this access, the threat actor archived the root directory of the web application, indicating an intent to obtain sensitive files such as
web.config. This was followed by host and network reconnaissance. -
The threat actor staged tooling in a public directory which included an:
-
Open-source network tunnel tool,
EARTHWORM -
Open-source remote access tool,
DWAGENT -
Open-source Active Directory (AD) reconnaissance tool,
SHARPHOUND
Local administrator accounts were created and used to dump SAM/SYSTEM hives in an attempt to compromise cached administrator credentials. The compromised credentials then enabled lateral movement via RDP.
DWAgent provided persistent remote access and was used for Active Directory reconnaissance.
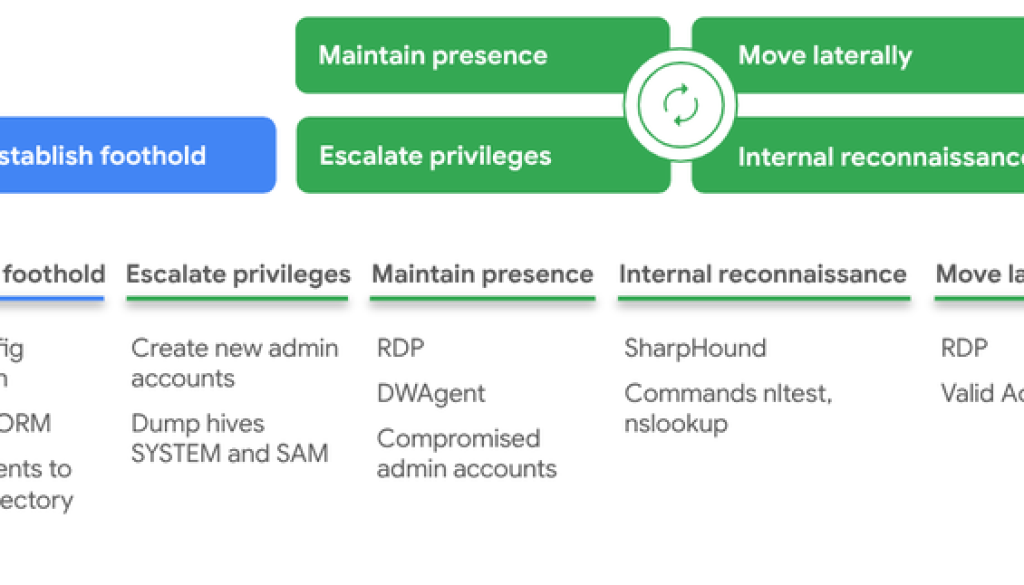
Figure 1: Attack lifecycle
Initial Compromise
External Reconnaissance
The threat actor began their operation by probing the victim’s web server with HTTP requests to various endpoints before ultimately shifting their attention to the /sitecore/blocked.aspx page. This page is a legitimate Sitecore component that simply returns a message if a request was blocked due to licensing issues. The page’s use of a hidden ViewState form (a standard ASP.NET feature), combined with being accessible without authentication, made it a potential target for ViewState deserialization attacks.
ViewState Deserialization Attack
ViewStates are an ASP.NET feature designed to persist the state of webpages by storing it in a hidden HTML field named __VIEWSTATE. ViewState deserialization attacks exploit the server’s willingness to deserialize ViewState messages when validation mechanisms are either absent or circumvented. When machine keys (which protect ViewState integrity and confidentiality) are compromised, the application effectively loses its ability to differentiate between legitimate and malicious ViewState payloads sent to the server.
Local web server (IIS) logs recorded that the threat actor’s attack began by sending an HTTP POST request to the blocked.aspx endpoint, which was met with an HTTP 302 “Found” response. This web request coincided with a “ViewState verification failed” message in Windows application event logs (Event ID 1316) containing the crafted ViewState payload sent by the threat actor:
Log: Application
Source: ASP.NET 4.0.30319.0
EID: 1316
Type: Information
Event code: 4009-++-Viewstate verification failed. Reason: Viewstate was
invalid.
<truncated>
ViewStateException information:
Exception message: Invalid viewstate.
Client IP: <redacted>
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1;
Trident/5.0) chromeframe/10.0.648.205 Mozilla/5.0
(Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko)
Chrome/121.0.0.0 Safari/537.36
PersistedState: <27760 byte encrypted + base64 encoded payload>
Referer:
Path: /sitecore/blocked.aspxMandiant recovered a copy of the server’s machine keys, which were stored in the ASP.NET configuration file web.config. Like many other ViewState deserialization attacks, this particular Sitecore instance used compromised machine keys. Knowledge of these keys enabled the threat actor to craft malicious ViewStates that were accepted by the server by using tools like the public ysoserial.net project.
Initial Host Reconnaissance
Mandiant decrypted the threat actor’s ViewState payload using the server’s machine keys and found it contained an embedded .NET assembly named Information.dll. This assembly, which Mandiant tracks as WEEPSTEEL, functions as an internal reconnaissance tool and has similarities to the GhostContainer backdoor and an information-gathering payload previously observed in the wild.
|
About WEEPSTEEL
|
The payload is designed to exfiltrate the following system information for reconnaissance:
// Code Snippet from Host Reconnaissance Function
Information.BasicsInfo basicsInfo = new Information.BasicsInfo
{
Directories = new Information.Directories
{
CurrentWebDirectory = HostingEnvironment.MapPath("~/")
},
// Gather system information
OperatingSystemInformation = Information.GetOperatingSystemInformation(),
DiskInformation = Information.GetDiskInformation(),
NetworkAdapterInformation = Information.GetNetworkAdapterInformation(),
Process = Information.GetProcessInformation()
};
// Serialize the 'basicsInfo' object into a JSON string
JavaScriptSerializer javaScriptSerializer = new JavaScriptSerializer();
text = javaScriptSerializer.Serialize(basicsInfo);Code snippet illustrating WEEPSTELL malware collection functionality
WEEPSTEEL appears to borrow some functionality from ExchangeCmdPy.py, a public tool tailored for similar ViewState-related intrusions. This comparison was originally noted in Kaspersky’s write-up on the GhostContainer backdoor. Like ExchangeCmdPy, WEEPSTEEL sends its output through a hidden HTML field masquerading as a legitimate __VIEWSTATE parameter, shown as follows:
<input type="hidden" name="__VIEWSTATE" id="__VIEWSTATE"
value="/wEPDwUKLTcyODc4{AES encrypted + base64 encoded output}" />Subsequent HTTP POST requests to the blocked.aspx endpoint from the threat actor would result in HTTP 200 “OK” responses, which Mandiant assesses would have contained an output in the aforementioned format. As the threat actor continued their hands-on interaction with the server, Mandiant observed repeated HTTP POST requests with successful responses to the blocked.aspx endpoint.
Establish Foothold
Following successful exploitation, the threat actor gained the NETWORK SERVICE privilege, equivalent to the IIS worker process w3wp.exe. This access provided the actor a starting point for further malicious activities.
Config Extraction
The threat actor then exfiltrated critical configuration files by archiving the contents of inetpubsitecoreSitecoreCDWebsite, a Sitecore Content Delivery (CD) instance’s web root. This directory contained sensitive files, such as the web.config file, that provide sensitive information about the application’s backend and its dependencies, which would help enable post-exploitation activities.
Host Reconnaissance
After obtaining the key server configuration files, the threat actor proceeded to fingerprint the compromised server through host and network reconnaissance, including but not limited to enumerating running processes, services, user accounts, TCP/IP configurations, and active network connections.
whoami
hostname
net user
tasklist
ipconfig /all
tasklist /svc
netstat -ano
nslookup <domain>
net group domain admins
net localgroup administratorsStaging Directory
The threat actor leveraged public directories such as Music and Video for staging and deploying their tooling. Files written into the Public directory include:
-
File: C:UsersPublicMusic7za.exe
-
Description: command-line executable for the 7-Zip file archiver
-
SHA-256: 223b873c50380fe9a39f1a22b6abf8d46db506e1c08d08312902f6f3cd1f7ac3
-
File: C:UsersPublicMusiclfe.ico
-
Description: An open-source network tunnel tool with SOCKS v5 server, tracked as
EARTHWORM -
SHA-256: b3f83721f24f7ee5eb19f24747b7668ff96da7dfd9be947e6e24a688ecc0a52b
|
About EARTHWORM
During our investigation,
|
-
File: C:UsersPublicMusic1.vbs
-
Description: Attack VBScript: Used to execute threat actor commands, its content varies based on the desired actions.
-
SHA-256: <hash varies>
|
In one instance where the file 1.vbs was retrieved, it contained a simple VBS code to launch the
|
Escalate Privileges
Following initial compromise, the threat actor elevated their access from NETWORK SERVICE privileges to the SYSTEM or ADMINISTRATOR level.
This involved creating local administrator accounts and obtaining access to domain administrator accounts. The threat actor was observed using additional tools to escalate privileges.
Adding Local Administrators
asp$: The threat actor leveraged a privilege escalation tool to create the local administrator account,asp$. The naming convention mimicking an ASP.NET service account with a common suffix $ suggests an attempt to blend in and evade detection.
"C:UsersPublicMusichelper.exe" "net user asp$ {REDACTED} /add"
"C:UsersPublicMusichelper.exe" "net localgroup administrators asp$ /add"sawadmin: At a later stage, the threat actor established aDWAGENTremote session to create a second local administrator account.
net user sawadmin {REDACTED} /add
net localgroup administrators sawadmin /addCredential Dumping
The threat actor established RDP access to the host using the two newly created accounts and proceeded to dump the SYSTEM and SAM registry hives from both accounts. While redundant, this gave the attacker the information necessary to extract password hashes of local user accounts on the system. The activities associated with each account are as follows:
asp$
reg save HKLMSYSTEM c:userspublicsystem.hive
reg save HKLMSAM c:userspublicsam.hivesawadmin: Prior to dumping the registry hives, the threat actor executedGoToken.exe. Unfortunately, the binary was not available for analysis.
GoToken.exe -h
GoToken.exe -l
GoToken.exe -ah
GoToken.exe -t
reg save HKLMSYSTEM SYSTEM.hiv
reg save HKLMSAM SAM.hivMaintain Presence
The threat actor maintained persistence through a combination of methods, leveraging both created and compromised administrator credentials for RDP access. Additionally, the threat actor issued commands to maintain long-term access to accounts. This included modifying settings to disable password expiration for administrative accounts of interest:
net user <AdminUser> /passwordchg:no /expires:never
wmic useraccount where name='<AdminUser>' set PasswordExpires=False For redundancy and continued remote access, the DWAGENT tool was also installed.
Remote Desktop Protocol
The actor used the Remote Desktop Protocol extensively. The traffic was routed through a reverse SOCKS proxy created by EARTHWORM to bypass security controls and obscure their activities. In one RDP session, the threat actor under the context of the account asp$ downloaded additional attacker tooling, dwagent.exe and main.exe, into C:Usersasp$Downloads.
|
File Path |
MD5 |
Description |
|
C:Usersasp$Downloadsdwagent.exe |
n/a |
DWAgent installer |
|
C:Usersasp$Downloadsmain.exe |
|
Downloaded from hxxp://130.33.156[.]194/main.exe |
Remote Access Tool: DWAGENT
DWAGENT is a legitimate remote access tool that enables remote control over the host. DWAGENT operates as a service with SYSTEM privilege and starts automatically, ensuring elevated and persistence access. During the DWAGENT remote session, the attacker wrote the file GoToken.exe. The commands executed suggest that the tool was used to aid in extracting the registry hives.
|
File Path |
MD5 |
Description |
|
C:UsersPublicMusicGoToken.exe |
|
Binary executed prior to dumping of SAM/SYSTEM hives. |
Table 2: File written in the DWAgent remote session
Internal Reconnaissance
Active Directory Reconnaissance
During a DWAGENT remote session, the threat actor executed commands to identify Domain Controllers within the target network. The actor then accessed the SYSVOL share on these identified DCs to search for cpassword within Group Policy Object (GPO) XML files. This is a well-known technique attackers employ to discover privileged credentials mistakenly stored in a weakly encrypted format within the domain.
nltest /DCLIST:<domain>
nslookup <domain-controller>
findstr /S /l cpassword
\<domain-controller>sysvoldcext.localpolicies*.xmlSHARPHOUND
The threat actor then transitioned to a new RDP session using a legitimate administrator account. From this session, SHARPHOUND , the data collection component for the Active Directory security analysis platform BLOODHOUND, was downloaded via a browser and saved to C:UsersPublicMusicsh.exe.
Following the download, the threat actor returned to the DWAGENT remote session and executed sh.exe, performing extensive Active Directory reconnaissance.
sh.exe -c allOnce the reconnaissance concluded, the threat actor switched back to the RDP session (still using the compromised administrator account) to archive the SharpHound output, preparing it for exfiltration.
C:Program Files7-Zip7zFM.exe
"C:UsersPublicMusic<number>_BloodHound.zip"Accounts Cleanup
With administrator accounts compromised, the earlier created asp$ and sawadmin accounts were removed, signaling a shift to more stable and covert access methods.
Move Laterally
The compromised administrator accounts were used to RDP to other hosts. On these systems, the threat actor executed commands to continue their reconnaissance and deploy EARTHWORM.
On one host, the threat actor logged in via RDP using a compromised admin account. Under the context of this account, the threat actor then continued to perform internal reconnaissance commands such as:
quser
whoami
net user <AdminUser> /domain
nltest /DCLIST:<domain>
nslookup <domain-controller>Recommendations
Mandiant recommends implementing security best practices in ASP.NET including implementing automated machine key rotation, enabling View State Message Authentication Code (MAC), and encrypting any plaintext secrets within the web.config file. For more details, refer to the following resources:
For detailed Sitecore remediation instructions, refer to the official Sitecore advisory SC2025-005.
Indicators of compromise
The following indicators of compromise are available in a Google Threat Intelligence (GTI) collection for registered users.
Accounts
|
Accounts |
Description |
|
asp$ |
Created account |
|
sawadmin |
Created account |
|
h496883 |
Workstation from the source of the RDP connection |
File-Based
|
MD5 |
SHA-256 |
Description |
|
117305c6c8222162d7246f842c4bb014 |
a566cceaf9a66332470a978a234a8a8e2bbdd4d6aa43c2c75c25a80b3b744307 |
WEEPSTEEL (Information.dll) |
|
a39696e95a34a017be1435db7ff139d5 |
b3f83721f24f7ee5eb19f24747b7668ff96da7dfd9be947e6e24a688ecc0a52b |
EARTHWORM (lfe.ico, ufp.exe, ufp.ico) |
|
f410d88429b93786b224e489c960bf5c |
n/a |
Helper.ico, helper.exe |
|
<hash varies> |
<hash varies> |
1.vbs |
|
be7e2c6a9a4654b51a16f8b10a2be175 |
n/a |
main.exe |
|
62483e732553c8ba051b792949f3c6d0 |
n/a |
GoToken.exe |
|
63d22ae0568b760b5e3aabb915313e44 |
61f897ed69646e0509f6802fb2d7c5e88c3e3b93c4ca86942e24d203aa878863 |
SharpHound |
Network-Based
| IP |
| 130.33.156[.]194:443 |
| 130.33.156[.]194:8080 |
| 103.235.46[.]102:80 |
Detections
Google Security Operations Enterprise and Enterprise+ customers can leverage the following product threat detections and content updates to help identify and remediate threats. All detections have been automatically delivered to Google Security Operations tenants within the Mandiant Frontline Threats curated detections ruleset. To leverage these updated rules, access Content Hub and search on any of the strings above, then View and Manage each rule you wish to implement or modify.
-
Earthworm Tunneling Indicators
-
User Account Created By Web Server Process
-
Cmd Launching Process From Users Music
-
Sharphound Recon
-
User Created With No Password Expiration Execution
-
Discovery of Privileged Permission Groups by Web Server Process
YARA Rule
rule G_Recon_WEEPSTEEL_1 {
meta:
author = "Mandiant"
strings:
$v_w = "<input type="hidden" name="__VIEWSTATE" id="__VIEWSTATE" value=" wide
$v_a = "<input type="hidden" name="__VIEWSTATE" id="__VIEWSTATE" value="
$v_b64_w = "<input type="hidden" name="__VIEWSTATE" id="__VIEWSTATE" value=" base64wide
$v_b64_a = "<input type="hidden" name="__VIEWSTATE" id="__VIEWSTATE" value=" base64
$s2 = "Services\Tcpip\Parameters" wide
$s3 = "GetOperatingSystemInformation"
$s4 = "GetSystemInformation"
$s5 = "GetNetworkAdapterInformation"
$s6 = "GetAllNetworkInterfaces"
$s7 = "GetIPProperties"
$s8 = "GetPhysicalAddress"
$s9 = "GetDomainNameFromRegistry"
$c1 = "Aes" fullword
$c2 = "CreateEncryptor" fullword
$c3 = "System.Security.Cryptography" fullword
$c4 = "ToBase64String" fullword
$guid = "6d5a95da-0ffe-4303-bb2c-39e182335a9f"
condition:
uint16(0) == 0x5a4d and
(
(all of ($c*) and 7 of ($s*)) or
($guid and (any of ($v*)))
)
}Acknowledgement
We would like to extend our gratitude to the Sitecore team for their support throughout this investigation. Additionally, we are grateful to Tom Bennett and Nino Isakovic for their assistance with the payload analysis. We also appreciate the valuable input and technical review provided by Richmond Liclican and Tatsuhiko Ito.
- aside_block
- <ListValue: [StructValue([(‘title’, ‘Contact Mandiant’), (‘body’, <wagtail.rich_text.RichText object at 0x3e858527d460>), (‘btn_text’, ”), (‘href’, ”), (‘image’, None)])]>
Read More for the details.