GCP – Now available: Cloud HSM as an encryption key service for Workspace client-side encryption
Organizations in highly-regulated sectors, such as government, defense, financial services, and healthcare, are required to meet stringent standards to safeguard sensitive data. Client-side encryption (CSE) for Google Workspace is a unique, privacy-preserving offering that keeps customer data confidential and enables the customer to be the sole arbiter of their data, helping them adhere to rigorous compliance regimes.
Google Workspace CSE adds another layer of encryption to your organization’s data — like files, emails, meetings, and events — in addition to the default encryption that Google Workspace provides. CSE can be especially beneficial for organizations that store sensitive and regulated data because it can provide:
-
Confidentiality for organizations working with sensitive intellectual property, healthcare records, and financial data.
-
Compliance support for organizations in highly-regulated industries that have ITAR and EAR requirements.
-
Data sovereignty for organizations that need demonstrative data control using encryption keys that can be held at a defined boundary, such as a specific geographic location or within a nation’s borders.
To help highly-regulated organizations meet their encryption key service obligation, we are now offering Cloud Hardware Security Module (HSM) for Google Workspace (CHGWS,) bringing Google Cloud’s highest levels of compliance classifications to Workspace CSE customers. Cloud HSM is a highly available and scalable, fully managed key management service operated at cloud scale with hardware-backed keys stored in FIPS 140-2 Level 3 compliant HSMs (hardware security modules).
Available today in the U.S., and globally in the coming months, CHGWS offers a convenient, flat pricing model that makes it easy to set up and maintain.
- aside_block
- <ListValue: [StructValue([(‘title’, ‘$300 in free credit to try Google Cloud security products’), (‘body’, <wagtail.rich_text.RichText object at 0x3e950b5c3970>), (‘btn_text’, ”), (‘href’, ”), (‘image’, None)])]>
Use Cloud HSM to help meet regulatory obligations
Cloud HSM is engineered to support cloud workloads that are subject to the most stringent security and regulatory mandates, and has undergone comprehensive audits and achieved compliance with regulations and certifications including FedRAMP High, DISA IL5, ITAR, SOC 1/2/3, and PCI DSS.
A cornerstone of Cloud HSM for Google Workspace’s security posture is its reliance on FIPS 140-2 Level 3 validated Marvell LiquidSecurity HSMs. Specifically, the service uses models CNL3560-NFBE-2.0-G and CNL3560-NFBE-3.0-G, running firmware versions 3.4 build 09. This validation level is critical, as it indicates that the cryptographic modules have met the highest standards of security for hardware and software components.
This extensive list of certifications provides strong assurance to customers in highly regulated market segments that their key management and data protection needs are met in accordance with the most demanding regulatory and compliance frameworks.

Our emphasis on comprehensive compliance can help simplify the burdens faced by these organizations, and can allow them to confidently deploy and manage their encryption keys while satisfying their legal and audit requirements.
While security and compliance are paramount, Google Cloud also recognizes the critical importance of high availability and scalability for its customers. CHGWS can help address these needs by offering a highly available and standards-compliant CSE key service that can be deployed rapidly, often in minutes.
Our rapid deployment capability, combined with inherent high availability, can help ensure that critical encryption services are always accessible, minimizing potential disruptions to operations.
How does Cloud HSM for Google Workspace work?
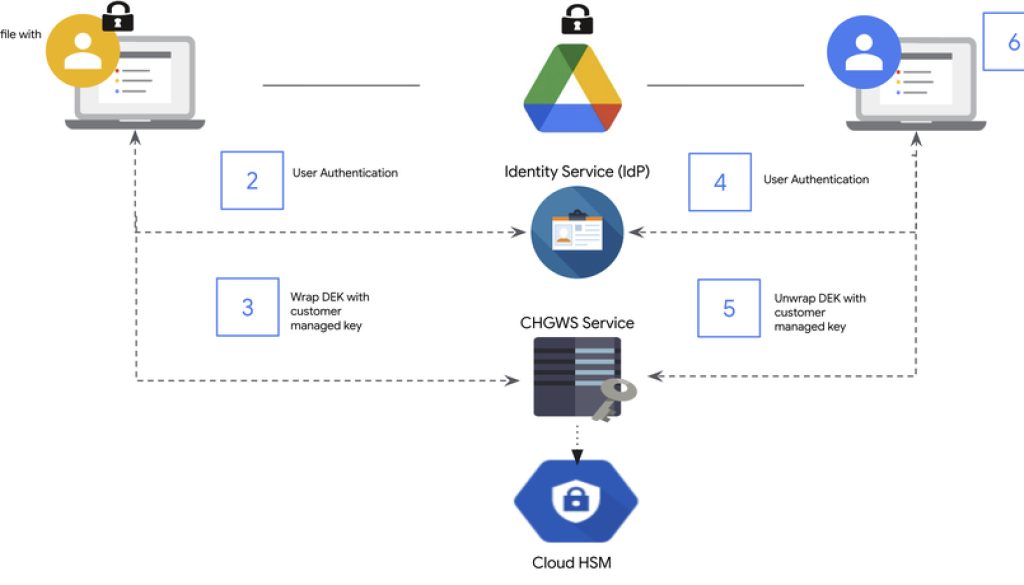
CHGWS can enhance privacy and compliance for Google Workspace CSE. The data is encrypted end-to-end and can only be decrypted by users who have permission to access it.
Encrypting data
Step 1: When a user creates content in Google Workspace, the CSE library generates a data encryption key (DEK) that is sent to the CHGWS service.
Step 2: The CHGWS service verifies the user’s identity using a customer-managed identity provider and Google Cloud IAM.
Step 3: The CHGWS service then encrypts the DEK using a customer-managed encryption key (CMEK) stored in Cloud HSM, and sends the encrypted DEK back. Then the CSE library encrypts the content using the DEK, and the encrypted DEK is stored with the content.
Reading encrypted data
When a user tries to access encrypted content the process unfolds in reverse.
Step 4: First, the CSE library sends the encrypted DEK stored with the content to CHGWS service. CHGWS service verifies the user’s identity using the customer-managed identity provider.
Step 5: CHGWS service uses the CMEK stored in Cloud HSM to decrypt the DEK, and sends it back.
Step 6: The CSE library uses the decrypted DEK to decrypt the content.
All the encrypt and decrypt operations using CMEK are always performed inside the HSM. The CMEK never leaves the HSM protection boundary to ensure that customers maintain full control over their encryption keys and data access.
Generating audit logs using Cloud Logging: As with all Google Cloud services, Cloud HSM service writes audit logs that record administrative activities and accesses in your Google Cloud resources. Audit logs help you answer “who did what, where, and when?” in your Google Cloud resources, with the same level of transparency as in on-premises environments. This is part of our comprehensive Access Transparency offering.
Enabling audit logs can help your security, auditing, and compliance entities monitor Google Cloud data and systems for possible vulnerabilities or external data misuse. You can learn more about KMS Audit Logging here.
Regional availability and our SLA
Our Cloud HSM service provides 99.95% uptime for encryption and decryption operations. You can review Cloud Key Management Service and Cloud HSM SLA for more details. To get started, please see our onboarding instructions.
Read More for the details.