GCP – Introducing the Emerging Threats Center in Google Security Operations
When a major vulnerability makes headlines, CISOs want to know fast if their organization is impacted and prepared. Getting the correct answer is often a time-consuming and human-intensive process that can take days or weeks, leaving open a dangerous window of unknown exposure.
To help close that gap, today we’re introducing the Emerging Threats Center in Google Security Operations. Available today for licensed customers in Google Security Operations, this new capability can help solve the core, practical problem of scaling detection engineering, and help transform how teams operationalize threat intelligence.
Enabled by Gemini, our detection-engineering agent responds to new threat campaigns detected by Google Threat Intelligence, and includes frontline insights from Mandiant, VirusTotal, and across Google. It generates representative events, assessing coverage, and closing detection gaps.
The Emerging Threats Center can help you understand if you are impacted by critical threat campaigns, and provides detection coverage to help ensure you are protected going forward.
Introducing campaign-based prioritization with emerging threats
Protecting against new threats has long been a manual, reactive cycle. It begins with threat analysts pouring over reports to identify new campaign activity, which they then translate into indicators of compromise (IoCs) for detection engineers. Next, the engineering team manually authors, tests, and deploys the new detections.
Too often, we hear from customers and security operations teams that this labor-intensive process leaves organizations swimming upstream. It was “hard to derive clear action from threat intelligence data,” according to 59% of IT and cybersecurity leaders surveyed in this year’s Threat Intelligence Benchmark, a commissioned study conducted by Forrester Consulting on behalf of Google Cloud.
By sifting through volumes of threat intelligence data, the Emerging Threats Center can help security surface the most relevant threat campaigns to an organization — and take proactive action against them.
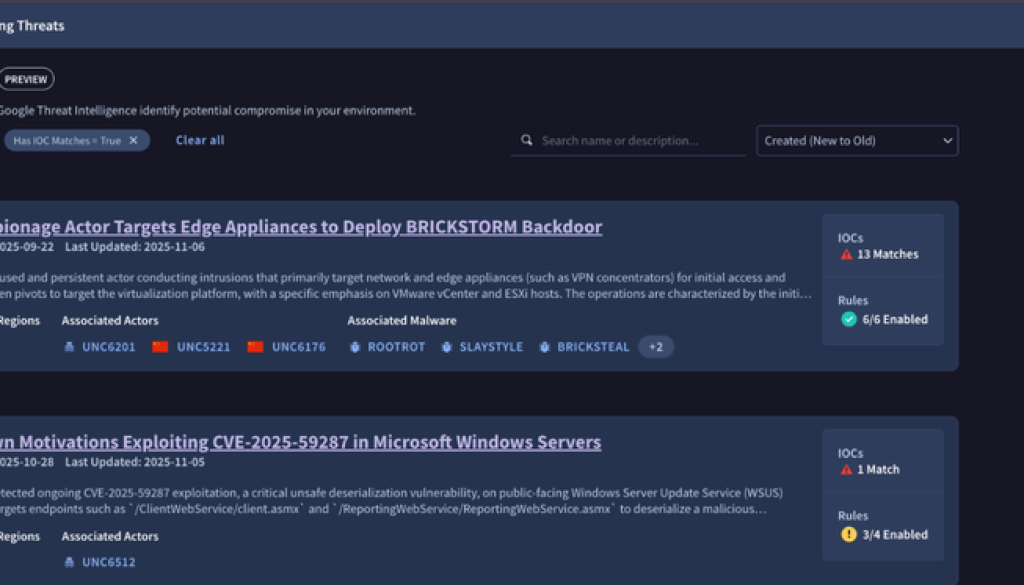
Instead of starting in a traditional alert queue, analysts now have a single view of threats that pose the greatest risks to their specific environment. This view includes details on the presence of IOCs in event data and detection rules.
For example, when a new zero-day vulnerability emerges, analysts don’t have to manually cross-reference blog posts with their alert queue. They can immediately see the campaign, the IOCs already contextualized against their own environment, and the specific detection rules to apply. This holistic approach can help them proactively hunt for the most time-sensitive threats before a major breach occurs.
Making all this possible is Gemini in Security Operations, transforming how we engineer detections. By ingesting a continuous stream of frontline threat intelligence, it can automatically test our detection corpus against new threats. When a gap is found, Gemini generates a new, fully-vetted detection rule for an analyst to approve. This systematic, automated workflow can help ensure you are protected from the latest threats.
Understanding exposure, detailing defensive posture
Our campaign-based approach can provide definitive answers to the two most critical questions a security team faces during a major threat event: How are we affected, and how well are we prepared.
How are we affected?
The first priority is to understand your exposure. The Emerging Threats Center can help you find active and past threats in your environment by correlating campaign intelligence against your data in two ways:
-
IOC matches: It automatically searches for and prioritizes campaign-related IoCs across the previous 12 months of your security telemetry.
-
Detection matches: It instantly surfaces hits from curated detection rules that have been mapped directly to the specific threat campaign.
Both matches provide a definitive starting point for your investigative workflow.
Emerging Threat Center Feed View
How are we prepared?
The Emerging Threat Center can also help prove that you are protected moving forward. This capability can provide immediate assurance of your defensive posture by helping you confirm two key facts:
-
That you have no current or past IOC or detection hits related to the campaign.
-
That you have the relevant, campaign-specific detections active and ready to stop malicious activity if it appears.
Emerging Threat Center Campaign Detail View
Under the hood: The detection engineering engine
The Emerging Threat Center is built on a resilient, automated system that uses Gemini models and AI agents to drastically shorten the detection engineering lifecycle.
Agentic Detection Engineering Workflow
Here’s how it works.
First, it ingests intelligence. The system automatically ingests detection opportunities from Google Threat Intelligence campaigns, which are sourced from Mandiant’s frontline incident response engagements, our Managed Defense customers, and Google’s unique global visibility. From thousands of raw sample events from adversary activity, Gemini is able to extract a distinct set of detection opportunities associated with the campaign.
Next, it generates synthetic events. We generate high-fidelity anonymized, synthetic event data that accurately mimics adversary tactics, techniques, and procedures (TTPs) described in the intelligence. We use an automated pipeline to generate a corpus of high-fidelity synthetic log events, providing a robust dataset for testing.
Then, it tests coverage. The system uses the synthetic data to test our existing detection rule set, providing a rapid, empirical answer to how well we are covered for a new threat. This automated testing pipeline quickly provides an answer on detection coverage.
After that, it accelerates rule creation. When coverage gaps are found, the process uses Gemini to automatically generate and evaluate new rules. Gemini drafts a new detection rule and provides a summary of its logic and expected performance, reducing the time to create a production-ready rule from days to hours.
Finally, it requires human review. The new rule is submitted to a human-in-the-loop security analyst who can vet and verify the new rule before deploying it. AI has helped us transform a best-effort, manual process into a systematic, automated workflow. By enabling us to tie new detections directly to the intelligence campaign it covers, we can help you be prepared for the latest threats.
“The real strategic shift is moving past those single indicators to systematically detecting underlying adversary behaviors — that’s how we get ahead and stay ahead. Out-of-box behavioral rules, based on Google’s deep intel visibility, help us get there,” said Ron Smalley, senior vice-president and head of Cybersecurity Operations, Fiserv.
To dive deeper into the complete framework that powers this, read more about our applied threat intelligence and watch our Google Security Talks keynote.
Read More for the details.