GCP – Innovate with Confidential Computing: Attestation, Live Migration on Google Cloud
Since its debut on Google Cloud, Confidential Computing has evolved at an incredible pace, offering customers robust protection for sensitive data processed in the cloud and ensuring higher levels of security and privacy.
Driven by the ever-increasing need to protect sensitive data in the cloud, we’ve innovated continuously, enhancing our services around two key pillars: robust attestation and live migration.
Google Cloud Attestation: Building the foundation of trust
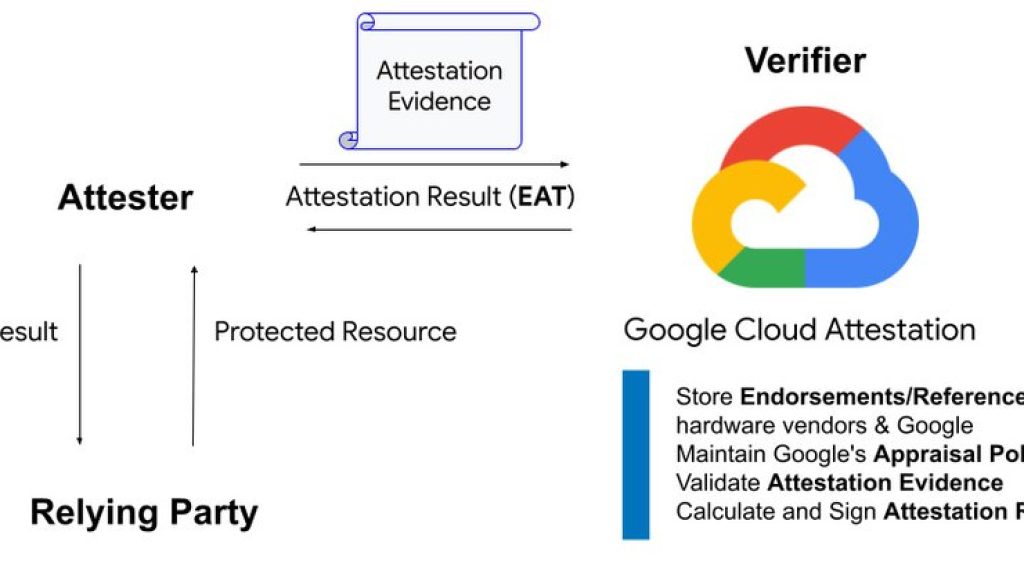
Attestation empowers customers with verifiable assurance of their cloud environment’s integrity, a critical need in today’s security landscape. It confirms that sensitive data is processed in rigorously vetted, hardware-backed Trusted Execution Environments (TEEs), enabling customers to confidently deploy and manage confidential workloads — knowing their data remains protected.
Google Cloud Attestation simplifies this process, offering a unified solution to remotely verify the trustworthiness of Confidential Computing environments, including those secured by Virtual Trusted Platform Module (vTPM) for AMD SEV and TDX Module for Intel Trust Domain Extensions (TDX). This provides customers with the necessary tools to help meet stringent compliance requirements and protect their most valuable data.
- aside_block
- <ListValue: [StructValue([(‘title’, ‘$300 in free credit to try Google Cloud security products’), (‘body’, <wagtail.rich_text.RichText object at 0x3e85007bf280>), (‘btn_text’, ‘Start building for free’), (‘href’, ‘http://console.cloud.google.com/freetrial?redirectPath=/welcome’), (‘image’, None)])]>
Attestation in action: Building confidence, layer by layer
Google Cloud Attestation doesn’t just take hardware vendors at their word. We work directly with them and apply our own stringent security standards. This rigorous process allows you to verify:
-
Genuine hardware: Your confidential workloads are running on authentic, untampered hardware.
-
Uncompromised environment: The TEE hasn’t been modified or compromised in any unauthorized way.
-
Strict security standards: Data processing within the TEE adheres to the highest security protocols.
This verification is made accessible through APIs, providing “claims tokens” that represent the attestation proof. Here’s a breakdown of the process:
-
Gather evidence: Google Cloud Attestation gathers evidence from your confidential environment.
-
Evaluate: This evidence is evaluated against endorsed values and Google’s internal security policies.
-
Generate claims: The results are converted into verifiable claims, formatted according to the IETF RATS EAT standard.
-
Sign cryptographically: Google Cloud Attestation provides cryptographically signed claims, ensuring their trustworthiness for services like secret release servers and identity and access management (IAM).
Google Cloud Attestation verifier service.
These cryptographic proofs can be validated in two ways, offering flexibility and enhanced privacy:
-
Using a public key: Validate by checking the well-known endpoint and using the public key from the
jwks_urifield. This works with OpenID Connect (OIDC) compatible applications. -
Using a root certificate: Download the root certificate from the
attestation-pki-rootwell-known endpoint (over HTTPS) and use it to validate the certificate chain. This option (usingtokenType: "PKI") enhances privacy by removing the possibility of the Attestation Verifier owner to collect IP address data, and also enables offline validation. A practical example of offline validation can be found in our PKI codelab.
Broad support, growing interoperability
Currently, Google Cloud Attestation supports:
-
Confidential VMs: Compute Engine VMs with hardware-based memory encryption.
-
Confidential GKE: Kubernetes nodes built on top of Confidential VMs, extending encryption-in-use to your containerized workloads.
-
Confidential Space: An isolated environment for operating on sensitive data, where data owners retain confidentiality. The workload runs on a hardened OS based on Container-Optimized OS.
The Attestation result, in the form of OpenID Connect tokens, is designed for interoperability. This means it can be used with cloud IAMs beyond Google Cloud IAM. For instance, a Confidential Space workload can present the Attestation Result to AWS Identity and Access Management, enabling secure multi-party collaboration where data or keys may reside in AWS.
“Attestation is an essential component of Confidential Computing and helps assure the integrity of the workload,” said Olivier Richaud, vice-president, Platforms and Site Reliability Engineering, Symphony. “With remote attestation we can prove to our end-customers that their data is processed inside of a Trusted Execution Environment where even we cannot access customer’s data.”
You can learn more about Google Cloud Attestation here.
Operator-independent attestation
Customers in highly-regulated industries including healthcare and Web3 may require third-party attestation that meets the “separation of duties” and Zero Trust requirements for the infrastructure provider and attestation provider.
For those customers, we added third-party verifier support with the Intel Tiber Trust Authority (ITA) to further the separation of duties. This latest collaboration between Intel and Google Cloud provides additional flexibility and strengthens trust across different security architectures.
Intel Tiber Trust Authority support is available for Intel TDX based Confidential VMs and Confidential Space running on the C3 machine family. We are also very excited to announce that ITA is a free service (with optional paid support) for Confidential Computing customers on Google Cloud.
“Intel is delighted to have partnered with Google Cloud to offer operator independent attestation through Intel Tiber Trust Authority for Google’s Confidential VMs and Confidential Space. This partnership aims to accelerate the broad adoption and scalability of Confidential Computing,” said Anand Pashupathy, vice-president and general manager, Intel Confidential Computing.
Smooth operations: Live migration for Confidential GKE nodes
While robust security is paramount, it shouldn’t come at the cost of operational efficiency. That’s why we’re thrilled to share the general availability of Live Migration for Confidential GKE Nodes using AMD SEV Confidential Computing technology running on N2D machines.
Traditionally, updating infrastructure with underlying privacy protections in place could be a disruptive process. Live Migration changes that. It enables the transfer of running workloads to different host machines — without service interruption.
How Live Migration works with Confidential Computing
Live Migration for Confidential GKE Nodes differs slightly from regular GKE node migrations. The key difference is the continuous encryption of memory pages during the transfer between the source and destination hosts. This is achieved through the hardware capabilities of AMD EPYC Milan processors.
While the hardware protects the memory, our cloud infrastructure coordinates the maintenance event transparently to your workload. Any existing AMD-SEV based Confidential GKE node cluster (on N2D machine family), once upgraded to a supported GKE version, will automatically have Live Migration enabled.
To begin using Confidential GKE Nodes with Live Migration, simply create your new Confidential GKE Nodes. Live Migration is enabled by default. Confidential VMs also support Live Migration.
The future of Confidential Computing
Google Cloud is committed to pushing the boundaries of Confidential Computing. By combining robust attestation with live migration, we’re empowering customers to protect their most sensitive data while maintaining operational agility.
To further highlight our commitment to security, today we are releasing the latest testing results for Confidential Space from NCC Group, an independent security assessment organization. It covers the latest improvements achieved by using Intel TDX, Intel Tiber Trust Authority, and a third-party key management and identity and access management system.
You can learn more about how you can use Confidential Computing here.
Read More for the details.