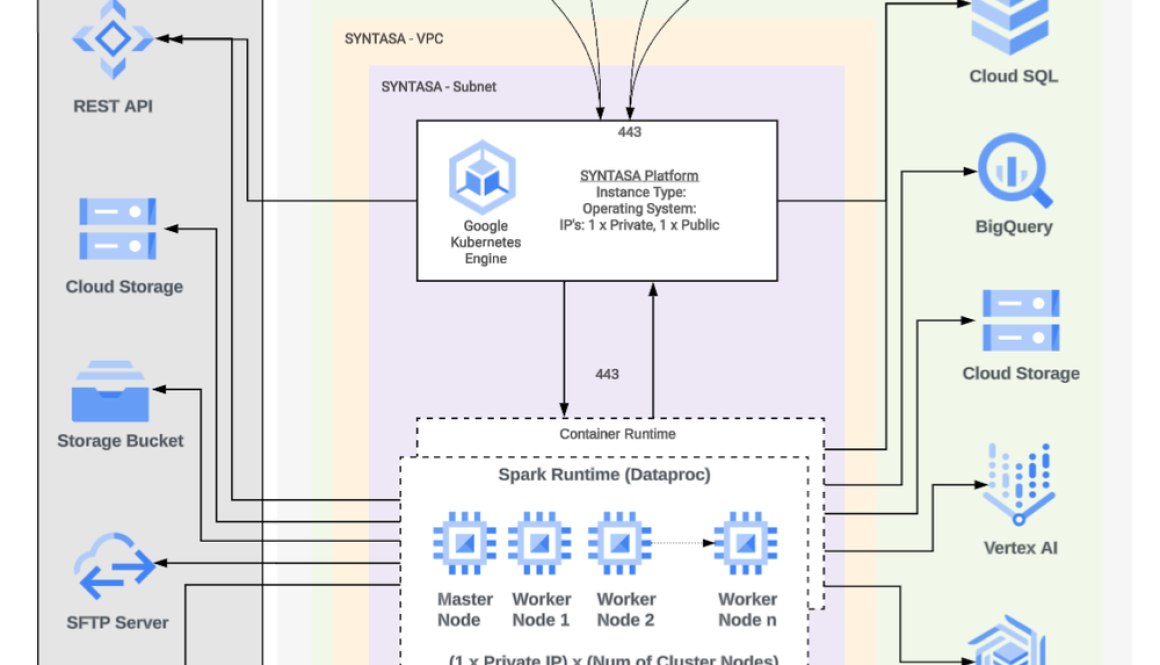
We have exciting news for Google Cloud partners: Today we’re announcing our new partner program, Google Cloud Partner Network, which will formally roll out in the first quarter of 2026.
This new program marks a fundamental shift in how we measure success and reward value. Applicable to all partner types and sizes – ISVs, RSIs, GSIs, and more – the new program reinforces our strategic move toward recognizing partner contribution across the entire customer lifecycle.
Google Cloud Partner Network is being completely streamlined to focus on real-world results. This marks a strategic shift from measuring program work to valuing genuine customer outcomes. This includes rewarding successful co-sell sales efforts, high-quality service delivery, and shared innovation with ISVs. We are also integrating AI into the program’s core to make partner participation much easier, allowing more focus on customers instead of routine program administration.
With its official kickoff in Q1, the new program will provide a six-month transition window for partners to adjust to the new framework. Today, we are sharing the first details of the Google Cloud Partner Network, which is centered on three pillars: simplicity, outcomes, and automation.
Simplicity
We’re making the program simpler by moving away from tracking the work of traditional program requirements, such as business plans and customer stories, and towards recognising partner contributions – including pre-sales influence, co-innovation, and post-sales support.
Because the program is designed to put the customer first, we’ve narrowed requirements to focus on partner efforts that deliver real, measurable value. For example, the program will recognize investments in skills, real-world experience, and successful customer outcomes.
Outcomes
The new program will provide clear visibility into how partner impact is recognized and rewarded, focusing on customer outcomes. Critical highlights include:
-
New tiers: We’re evolving from a two-tier to a three-tier model: Select, Premier, and a new Diamond tier. Diamond is our highest distinction – it is intentionally selective, reserved for the few partners who consistently deliver exceptional customer outcomes. Each tier will now reflect our joint customer successes and will be determined based on exceptional customer outcomes across Google Cloud and Google Workspace.
-
New baseline competencies: A new competency framework marks a fundamental shift that will replace today’s specializations, in order to reward partners for their deep technical and sales capabilities. The framework focuses on a partner’s proven ability to help customers, measuring two key dimensions: capacity (knowledge and skills development, validated by technical certifications and sales credentials) and capability (real-world success, measured by pre-sales and post-sales contributions to validated closed/won opportunities). This framework operates independently from tiering to allow partners to earn a competency without any dependency on a program tier.
-
New advanced competency: The new global competencies introduce a second level of achievement, Advanced Competency, to signal a higher designation.
Automation
Building on the proven success and transparency delivered through tools like the Earnings Hub and Statement of Work Analyzer, today’s Partner Network Hub will transform to deliver automation and transparency across the program.
The administrative responsibility for partners to participate in the program will be dramatically reduced through the use of AI and other tools. For example, a key change is the introduction of automated tracking across tiering and competency achievements. We will automatically apply every successful customer engagement toward a partner’s progress in all eligible tiers and competencies. This radical simplification eliminates redundant reporting and ensures seamless, comprehensive recognition for the outcomes delivered.
What’s next…
The new program and portal will officially launch in Q1 2026, enabling partners to immediately log in, explore benefits and differentiation paths, and begin achieving new tiers and competencies. To ensure a smooth transition, we will host a series of webinars and listening sessions throughout early next year to educate partners on Google Cloud Partner Network.
Stay tuned. We’ll have more to share soon!
for the details.