GCP – How to secure your remote MCP server on Google Cloud
As enterprises increasingly adopt model context protocol (MCP) to extend capabilities of AI models to better integrate with external tools, databases, and APIs, it becomes even more important to ensure secure MCP deployment.
MCP unlocks new capabilities for AI systems; it can also introduce new risks, such as tool poisoning, prompt injection, and dynamic tool manipulation. These can lead to data exfiltration, identity subversion and misuse of AI systems.
Securing an MCP deployment begins with a strong security foundation. Here are five key MCP deployment risks you should be aware of, and how using a centralized proxy architecture on Google Cloud can help mitigate them.
Top five MCP deployment risks you should know
While there are some broader risks unique to AI, these five are especially important to be aware of when designing MCP deployments:
-
Unauthorized tool exposure: A misconfigured MCP manifest can create a vulnerability that allows unauthorized individuals or agents to access sensitive tools, such as internal administration functions.
-
Session hijacking: An attacker may steal a legitimate user’s session ID to impersonate them. This allows the attacker to either make unauthorized API calls directly or, in stateful systems, inject malicious payloads into a shared data queue for delivery to the victim’s active session.
-
Tool shadowing and shadow MCP: Rogue MCP tools, mimicking legitimate services, can be deployed by malicious actors. This deceptive practice can trick both AI agents and human employees into interacting with harmful tools under the belief they are genuine.
-
Sensitive data exposure and token theft: Improperly configured environments or inadequate data-handling practices can lead to the accidental exposure of sensitive information, such as API keys, credentials, tokens, and personally identifiable information (PII). Attackers can exploit exposed credentials to gain unauthorized access to corporate resources, which could lead to significant data breaches.
-
Authentication bypass: Weak, misconfigured, or inadequately-enforced authentication mechanisms can be exploited by attackers to circumvent security controls, allowing them to gain unauthorized access by successfully impersonating legitimate users and trusted entities.
- aside_block
- <ListValue: [StructValue([(‘title’, ‘$300 in free credit to try Google Cloud security products’), (‘body’, <wagtail.rich_text.RichText object at 0x7f53708dba60>), (‘btn_text’, ”), (‘href’, ”), (‘image’, None)])]>
How a centralized MCP proxy architecture can help
To address these core risks in a scalable manner, we recommend a pattern built around a centralized MCP proxy that acts as a secure intermediary for all communication between clients and MCP servers.
Built on Cloud Run, Apigee, or Google Kubernetes Engine, this intelligent proxy intercepts all tool calls, enforcing your organization’s security policies and providing extensive monitoring. By serving as a centralized security enforcement point, the MCP proxy enables important risk-managing capabilities such as consistent access controls (acts as an authorization server), advanced traffic management, audit logging, secret scanning, resource limits, and real-time threat detection, all without requiring modifications to individual remote MCP servers.
Without centralization, organizations deploying MCP servers face challenges:
-
Fragmented authentication: Each MCP server enforces its own policies, creating inconsistencies.
-
Operational overhead: Updating agents with new endpoints is extensive and error-prone.
-
Security blind spot: Limited visibility into health, usage, and anomalies across distributed MCP servers.
-
Expended attack surface: Vulnerabilities such as prompt injection, tool poisoning, and unmonitored traffic flows.
A unified MCP proxy on Google Cloud addresses these challenges by:
-
Enforcing organizational security policies at a single, managed entry point for all MCP requests and responses.
-
Authenticating and authorizing consistently using the Google Identity Platform.
-
Centralizing observability through Cloud Logging and Security Command Center.
-
Standardizing protections against threats, aligned with Google secure AI agent guide and OWASP guidance for agentic AI applications.
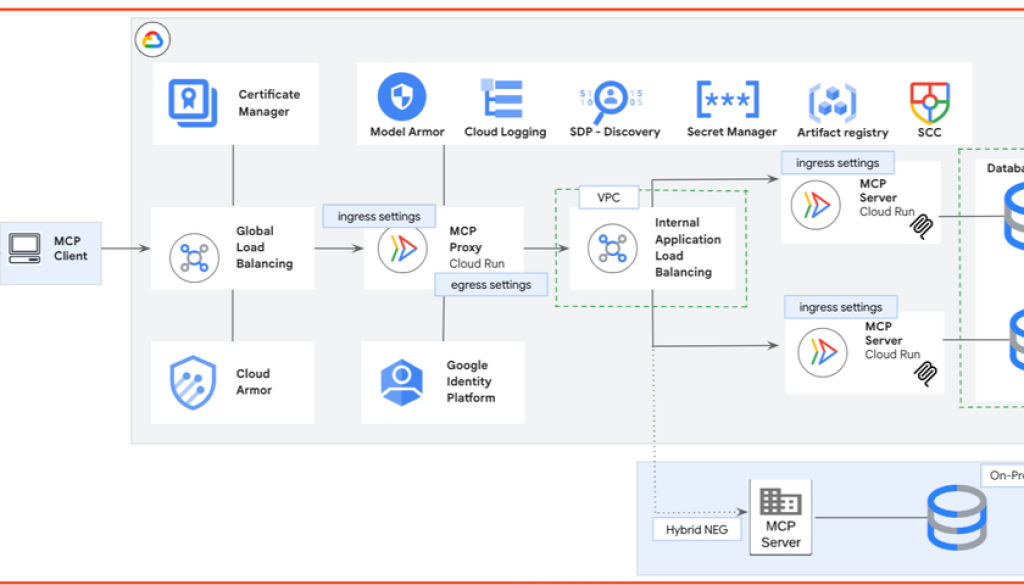
Architecture overview
The following reference architecture shows how Google Cloud services help secure MCP client requests end-to-end.
Layered security controls on Google Cloud.
Key components:
-
Global Load Balancing provides a single entry point for all MCP client traffic.
-
Certificate Manager manages TLS certificates for secure communication.
-
Cloud Armor provides DDoS and WAF protections against common OWASP web threats.
-
MCP Proxy acts as the central enforcement layer for authentication, authorization, request inspection, and routing.
-
Google Identity Platform validates identities and issues OAuth 2.0 tokens.
-
Model Armor screens model prompts and responses for prompt injection and jailbreak detection, sensitive data, and can help ensure responsible AI practices.
-
Secret Manager stores API keys, database credentials, and sensitive configuration values.
-
Artifact Registry ensures MCP server images are scanned, verified and encrypted at rest with customer managed encryption keys.
-
Internal Load Balancing routes sanitized traffic to the appropriate MCP servers.
-
Cloud Logging and Security Command Center deliver visibility, anomaly detection, and compliance reporting.
Layered security controls
Google Cloud applies security at every layer of the architecture. Let’s dig into these capabilities below.
Network-level security control
-
Network segmentation can isolate MCP tools servers, load balancers, and databases using virtual private networks (VPC), Cloud Run ingress, and Cloud Run egress options to reduce lateral movement risk.
-
Web attack and DDOS protection can help block malicious traffic, enforce IP allow and deny lists, and provide resilience against DDoS attacks with Global Load Balancer with Cloud Armor.
-
Advanced traffic management can help provide custom domain path matching for MCP tool servers, using Internal Application Load Balancer (ALB) with advanced traffic management capabilities. By inspecting the incoming request host and path, the ALB intelligently directs requests to the appropriate backend service or instance of your MCP server.
The backend service supports various back end types which can be MCP servers deployed in Google Cloud (such as VMs, Cloud Run, and Google Kubernetes Engine), in a remote network (using hybrid NEG) or on the internet (using internet NEG).
Advanced Traffic Management uses Internal Application Load Balancer to help provide custom domain path matching for MCP tool servers.
- code_block
- <ListValue: [StructValue([(‘code’, ‘defaultService: projects/PROJECT_ID/global/backendServices/mcp-tool-weatherrn name: matcher1rn routeRules:rn – matchRules:rn – prefixMatch: /weatherrn priority: 1rn routeAction:rn weightedBackendServices:rn – backendService: projects/PROJECT_ID/global/backendServices/mcp-tool-weatherrn weight: 100rn urlRewrite:rn pathPrefixRewrite: “/new-path-1/”rn hostRewrite: “new-host-name.com” rn – matchRules:rn – prefixMatch: /mathrn priority: 2rn routeAction:rn weightedBackendServices:rn – backendService: projects/PROJECT_ID/global/backendServices/mcp-tool-mathrn weight: 101rn urlRewrite:rn pathPrefixRewrite: “/new-path-2/”rn hostRewrite: “new-host-name.com”‘), (‘language’, ”), (‘caption’, <wagtail.rich_text.RichText object at 0x7f53713be520>)])]>
Authentication and authorization
The MCP proxy functions as the MCP Authorization Service (MAS) and integrates with an external Identity provider (such as Google Identity Platform, Okta, and Entra ID). This allows for secure access to your MCP server without the need to build and maintain a complex identity system.
This highly scalable and reliable authentication solution can help users securely authenticate through their existing identity platform. Additionally, Cloud Identity and Access Management (IAM) can enable enforcement of role-based access, and restrict access to cloud resources.
MCP authentication and authorization flow.
Protection in-line MCP client prompt and response with Model Armor
Proxy leverages Model Armor to provide robust, real-time protection against runtime threats like prompt injection, jailbreaking, tool poisoning, dynamic tool manipulation, and sensitive data leakage.
Using Model Armor templates, you can configure the MCP client prompts to be scrutinized and sanitized by Model Armor before being forwarded to the application load balancer. This process ensures that only sanitized prompts reach your MCP tools servers, thereby preventing unintended actions.
In-line protection with Model Armor.
- code_block
- <ListValue: [StructValue([(‘code’, ‘filterConfig:rn maliciousUriFilterSettings:rn filterEnforcement: ENABLEDrn piAndJailbreakFilterSettings:rn confidenceLevel: MEDIUM_AND_ABOVErn filterEnforcement: ENABLEDrn raiSettings:rn raiFilters:rn – confidenceLevel: MEDIUM_AND_ABOVErn filterType: HATE_SPEECHrn – confidenceLevel: MEDIUM_AND_ABOVErn filterType: DANGEROUSrn – confidenceLevel: MEDIUM_AND_ABOVErn filterType: SEXUALLY_EXPLICITrn – confidenceLevel: MEDIUM_AND_ABOVErn filterType: HARASSMENTrn sdpSettings:rn basicConfig:rn filterEnforcement: ENABLEDrnname: projects/project-id/locations/location/templates/MCP-Proxy-templaterntemplateMetadata:rn multiLanguageDetection:rn enableMultiLanguageDetection: true’), (‘language’, ”), (‘caption’, <wagtail.rich_text.RichText object at 0x7f53713be640>)])]>
Logging and auditing
All actions performed by MCP clients will be logged by the proxy to Cloud Logging, such as accessing specific tools, modifying or writing to memory locations, initiating or receiving communication. The log will include a timestamp, agent ID, session ID, payload, and input/output signature fingerprints.
The comprehensive nature of these logs, combined with the detailed metadata, can help administrators and auditors collect the necessary information to reconstruct client activities, identify anomalies, and enforce security policies effectively.
Additional security controls
In addition to layered security controls, a robust defense-in-depth strategy requires continuous monitoring and proactive measures to identify and mitigate threats.
Secrets scanning with Sensitive Data Protection
Sensitive Data Protection (SDP) discovery periodically scans the MCP Tools server on Cloud Run, specifically targeting the detection of hardcoded secrets. This proactive measure involves regular scans of the server’s build and runtime environment variables.
These scans detect insecure coding-practice risks, such as instances where sensitive information (including API keys, database credentials, and access tokens) has been inadvertently embedded directly in the code or configuration.
Vulnerability scanning
MCP server images stored in Artifact Registry are scanned for vulnerabilities before they are deployed. When a new image is pushed to Artifact Registry, it is automatically scanned for known vulnerabilities, providing actionable insights into potential weaknesses.
You can enforce policies that block the deployment of images with critical vulnerabilities as part of securing your environment from the ground up.
Threat detection
Security Command Center (SCC) provides AI protection that helps manage the security posture of your AI workloads by detecting threats and helping with mitigating risks to AI asset inventories. This includes managing threats to the MCP deployment through detection, investigation, and response.
SCC can also identify unauthorized access and data exfiltration attempts, delivering real-time alerts and remediation recommendations.
AI Protection helps you manage the security posture of your AI workloads by detecting threats and helping you to mitigate risks to your AI asset inventory.
Bring it all together
By strategically implementing these Google Cloud security services, you can establish a secure and resilient environment for your Model Context Protocol remote servers. Prioritizing authentication, network security, data protection, and continuous monitoring will ensure the integrity and confidentiality of your AI models and the sensitive information they process.
This unified, Zero Trust approach can help mitigate emerging AI-specific risks, and also provide a scalable and future-proof foundation for the evolution of your AI-driven applications.
To learn more about securing your AI workload, please refer to our documentation.
Read More for the details.